
The Role of Ethical Hacking in Strengthening Cybersecurity
By Ankita Das

Ethical hacking is a vital practice in the current cybersecurity environment, aimed at identifying and mitigating vulnerabilities in systems and networks. This discipline began gaining traction in the late 1990s as organizations recognized the necessity for proactive security measures. Ethical hackers, or “white-hat hackers,” utilize the same techniques as malicious hackers but with permission to enhance security. Notably, a 2024 survey revealed that 95% of ethical hackers are likely to retest vulnerabilities they report, showcasing their commitment to improving cybersecurity.
Ethical hacking has become integral to comprehensive security strategies across various sectors as cyber threats evolve. Companies like Google and Facebook actively employ ethical hackers through bug bounty programs to uncover system vulnerabilities. The proactive nature of ethical hacking helps prevent costly data breaches and fosters a culture of security awareness within organizations. Ethical hackers play a crucial role in safeguarding sensitive information by continuously assessing and improving security measures.
What is Ethical Hacking?
Ethical hacking refers to authorized practices identifying system, application, and network vulnerabilities. This discipline began gaining traction in the late 1990s as organizations recognized the need for proactive security measures. Ethical hackers, often called “white-hat hackers,” use the same techniques as malicious hackers but with permission to improve security.
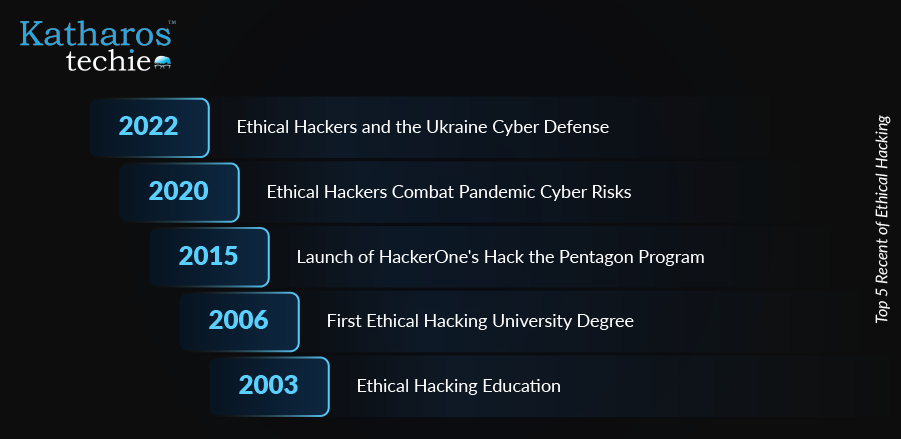
The origin of ethical hacking can be traced back to the emergence of computer networks and the internet in the 1960s and 1970s. Initially, “hackers” were individuals exploring systems to enhance functionalities without malicious intent. However, as technology advanced, the potential for exploitation became evident. Additionally, introducing CISSP certification in 1994 helped establish standards for cybersecurity professionals, including ethical hackers.
Currently, ethical hacking is integral to cybersecurity strategies across various sectors. Companies like Google and Facebook implement bug bounty programs to incentivize ethical hackers to find system vulnerabilities. According to a 2024 survey, 95% of ethical hackers are likely to retest vulnerabilities they reported. This data demonstrates the commitment of ethical hackers to improve security.
Looking ahead, the future of ethical hacking appears promising. With the rise of artificial intelligence and machine learning, ethical hackers will increasingly rely on advanced tools for vulnerability detection. As cyber threats evolve, organizations will increasingly focus on hiring skilled ethical hackers to prevent potential attacks. The proactive nature of ethical hacking positions it as a cornerstone of effective cybersecurity practices.
What is the Importance of Ethical Hacking?

Ethical hacking is essential for enhancing organizational security against cyber threats. Detecting vulnerabilities early helps organizations prevent data breaches. For example, a 2023 report showed that companies using ethical hacking saw 30% fewer security incidents than those that did not.
Moreover, ethical hacking helps organizations comply with industry regulations such as GDPR and HIPAA. Compliance protects sensitive data and helps organizations avoid hefty fines for data breaches. For instance, Target faced a $18.5 million settlement due to a data breach that could have been mitigated through effective ethical hacking measures.
Additionally, ethical hackers raise awareness among employees regarding cybersecurity risks. By conducting simulated phishing attacks or social engineering tests, they educate staff on best practices for safeguarding information. This proactive training approach significantly reduces human error-related vulnerabilities.
Benefits of Ethical Hacking in Cybersecurity

1. Proactive Vulnerability Identification
Ethical hacking identifies system vulnerabilities before malicious hackers can exploit them. This proactive approach significantly reduces the risk of costly data breaches. Organizations can save substantial amounts by addressing vulnerabilities using penetration testing tools like Metasploit or Burp Suite. Conducting these simulations regularly allows for early detection of weaknesses, which can prevent damage from cyberattacks.
2. Enhanced Security Posture
Regular ethical hacking assessments improve an organization’s overall security posture. Organizations can engage certified ethical hackers to perform red team exercises, which mimic real-world attacks. By continuously testing and strengthening security measures, organizations build resilience against evolving cyber threats. This ongoing improvement helps maintain robust defenses against potential attacks.
3. Compliance with Regulations
Ethical hacking helps organizations comply with industry regulations like GDPR and HIPAA. Adhering to these standards helps businesses avoid legal penalties and protect their reputation. Compliance demonstrates a commitment to protecting sensitive data and maintaining customer trust. Regular ethical hacking assessments are crucial for uncovering security gaps and maintaining compliance.
4. Protection Against Financial Losses
Data breaches can cost organizations millions in recovery efforts and lost revenue. Ethical hacking mitigates these risks by identifying and fixing vulnerabilities before attackers can exploit them. This preventative measure ultimately protects the organization’s financial stability.
5. Building Customer Trust
Demonstrating a commitment to cybersecurity through ethical hacking enhances customer trust and fosters loyalty. Customers are more likely to engage with brands that actively protect their information. Therefore, regular security assessments must be encouraged to reassure customers that their information is protected. It also helps build a reputation for reliability and responsibility in handling sensitive data.
6. Improved Incident Response Plans
Ethical hacking simulates real-world attacks, allowing organizations to test their incident response plans. This practice helps identify weaknesses in response strategies. It also enables businesses to refine their protocols for better prep against attacks.
7. Cost-Effective Security Enhancements
While ethical hacking involves initial costs, it is a cost-effective strategy in the long run. Preventing data breaches and system compromises helps organizations save on recovery costs and protect their reputation. Moreover, ethical hacking enables targeted resource allocation. This ensures that cybersecurity investments are focused on the most critical vulnerabilities.
Key Functions of Ethical Hackers

Ethical hackers play a crucial role in strengthening an organization’s cybersecurity posture. Their responsibilities encompass various functions that help identify vulnerabilities, mitigate risks, and enhance security. Below are ten key functions of ethical hackers:
1. Reconnaissance and Information Gathering
Ethical hackers begin their assessments by gathering information about the target system. This phase involves passive and active reconnaissance methods, such as searching public databases and using network scanning tools. Hackers use tools like Nmap to gather data on open ports and services. This initial information is vital for planning further testing phases and understanding potential attack vectors.
2. Scanning and Enumeration
After completing reconnaissance, ethical hackers scan and enumerate the system to identify vulnerabilities. They use tools like Nessus for vulnerability scanning and service enumeration to discover weaknesses. Early identification allows the organization to patch vulnerabilities before malicious hackers target them.
3. Gaining Access
Ethical hackers simulate attacks to gain unauthorized access to systems, mimicking the techniques used by malicious hackers. They exploit identified vulnerabilities using tools like Metasploit. For example, an ethical hacker tested a retail company’s e-commerce platform by exploiting an SQL injection vulnerability, gaining access to sensitive customer data. This demonstration prompted the company to implement stronger input validation measures.
4. Maintaining Access
After gaining access, ethical hackers may attempt to maintain their foothold within the system to evaluate how easily attackers could do the same. This can involve creating backdoors or installing rootkits for further testing. In this case, an ethical hacking team demonstrates how easily they can maintain access to a corporate network by installing a backdoor during a penetration test. This exercise highlights the need for improved monitoring and intrusion detection systems.
5. Clearing Tracks
Ethical hackers ensure their activities do not leave traces that could alert system administrators or security teams. They practice techniques to clear logs and cover their tracks after testing. This process also demonstrates how sophisticated attackers might evade detection. Clearing tracks emphasizes the importance of robust logging mechanisms for identifying real threats.
6. Reporting Findings
One of the key responsibilities of ethical hackers is to document their findings from assessments. They prepare detailed reports outlining vulnerabilities discovered, methods used, and recommendations for remediation. The organization receives a thorough report from ethical hackers after a security assessment, which includes prioritized action items for addressing vulnerabilities. This report served as a roadmap for enhancing their security measures.
7. Remediation Assistance
Ethical hackers often assist organizations in remediating identified vulnerabilities by guiding best practices and security enhancements. After identifying weaknesses in a technology company’s infrastructure, ethical hackers work closely with the IT team to implement necessary patches and configuration changes. Their collaboration ensures that security measures are effectively integrated into existing systems.
8. Security Awareness Training
Ethical hackers also play a role in educating employees about cybersecurity best practices through training sessions. They highlight common attack vectors such as phishing and social engineering tactics employed by attackers.
9. Compliance Audits
Many organizations must comply with industry regulations regarding data protection and cybersecurity practices. Ethical hackers conduct compliance audits to ensure adherence to standards such as GDPR or HIPAA. Generally, an ethical hacking team evaluates an organization’s systems against HIPAA requirements, identifying gaps that could lead to non-compliance fines. This evaluation helps the organization align its practices with regulatory expectations.
10. Continuous Improvement
Finally, ethical hackers contribute to continuous improvement in an organization’s security posture by regularly reassessing systems and updating security protocols based on emerging threats. They conduct periodic penetration tests to ensure that defenses remain robust against evolving cyber threats.
Ethical hackers perform essential functions that significantly contribute to an organization’s cybersecurity efforts. By identifying vulnerabilities, assisting in remediation, providing training, and ensuring compliance with regulations, they help organizations protect sensitive data from malicious attacks effectively. Their proactive approach mitigates risks and promotes a culture of security awareness within organizations.